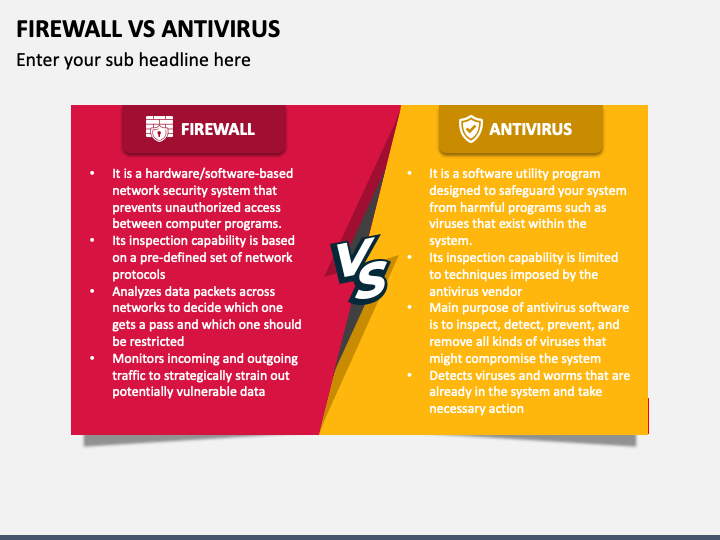
Endpoint security encompasses all devices within a network, while antivirus targets malware, and firewalls block unauthorized access. Each serves a distinct but complementary role in cybersecurity.
In today’s digital landscape, protecting sensitive data is crucial. Endpoint security offers comprehensive protection for all network-connected devices, ensuring they are secure. Antivirus software focuses on detecting and eliminating malicious software, safeguarding individual systems. Firewalls act as a barrier, preventing unauthorized access to the network.
Understanding these differences helps businesses implement a layered security strategy. By combining endpoint security, antivirus, and firewalls, organizations can defend against diverse cyber threats effectively. This multi-faceted approach strengthens overall cybersecurity, providing peace of mind in an increasingly connected world.
Credit: www.xcitium.com
What Is Endpoint Security?
Endpoint Security is a crucial part of modern cybersecurity. It protects devices like computers, smartphones, and tablets from cyber threats. These devices are known as endpoints. Endpoint Security ensures that each of these devices is safe from malware, viruses, and unauthorized access.
Definition
Endpoint Security refers to the protection of devices connected to a network. These devices can be laptops, smartphones, tablets, and desktops. The goal is to secure each endpoint from potential cyber threats. This involves a combination of software, policies, and procedures to safeguard the network.
Key Features
| Feature | Description |
|---|---|
| Antivirus | Scans and removes malicious software. |
| Firewall | Monitors incoming and outgoing network traffic. |
| Data Encryption | Encrypts data to protect sensitive information. |
| Device Management | Controls and monitors device settings and usage. |
| Threat Detection | Identifies and alerts on potential threats. |
- Real-time Protection: Monitors and protects in real-time.
- Automated Updates: Ensures the latest security patches are applied.
- Access Control: Manages who can access the network and devices.
- Incident Response: Provides tools to respond to security incidents.
What Is Antivirus?
Antivirus software is a crucial component in the world of cybersecurity. It helps protect your computer from malicious software. This software can detect, prevent, and remove viruses. Antivirus solutions have evolved over the years, offering more advanced features.
Definition
An antivirus is a program designed to detect and eliminate malware. Malware includes viruses, worms, trojans, and more. The primary goal is to prevent and remove harmful software. It ensures your computer stays safe from cyber threats.
Key Features
- Real-time scanning: Antivirus software checks files as they are accessed. This helps in identifying threats immediately.
- Automatic updates: Regular updates keep the antivirus effective. It ensures the program can recognize new threats.
- System scans: Scheduled or manual scans check the entire system. This helps in finding and removing hidden malware.
- Heuristic analysis: This feature identifies new or unknown threats. It analyzes the behavior of files and programs.
- Quarantine: Suspicious files are isolated. This prevents them from causing harm until they are reviewed.
- Virus definitions: A database of known virus signatures. The antivirus uses this to identify and remove threats.
Antivirus software is essential for basic cybersecurity. It protects your system from a wide range of threats.
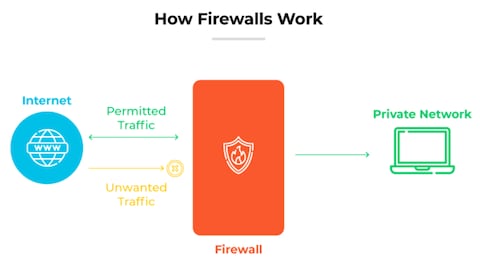
What Is A Firewall?
A firewall is a security device. It monitors and controls incoming and outgoing network traffic. Firewalls create a barrier between trusted and untrusted networks. They help protect your system from cyber threats.
Definition
A firewall is a network security system. It acts as a gatekeeper. Firewalls use predefined rules to allow or block data. This ensures that only safe data enters your network.
Key Features
- Packet Filtering: Examines packets and decides their fate.
- Proxy Service: Acts as an intermediary for requests.
- Stateful Inspection: Tracks the state of active connections.
- Unified Threat Management (UTM): Combines multiple security features.
- Virtual Private Network (VPN) Support: Secures remote access.
| Feature | Description |
|---|---|
| Packet Filtering | Filters traffic based on packet information. |
| Proxy Service | Intermediary for client requests to servers. |
| Stateful Inspection | Monitors active connections and data flow. |
| Unified Threat Management | Combines multiple security functions in one device. |
| VPN Support | Allows secure remote access to the network. |
Credit: www.paloaltonetworks.com
Comparing Endpoint Security, Antivirus, And Firewall
Understanding the differences between Endpoint Security, Antivirus, and Firewall is crucial. Each plays a unique role in protecting your devices and network. This guide will help clarify their scope, performance impact, and benefits.
Protection Scope
Antivirus software focuses on detecting and removing malware. It scans files and applications for known threats.
- Protects against viruses, worms, and Trojans.
- Primarily focuses on individual devices.
Firewall acts as a barrier between your network and external threats. It monitors incoming and outgoing traffic.
- Blocks unauthorized access to the network.
- Filters traffic based on predefined rules.
Endpoint Security encompasses a broader range of protections. It includes antivirus, firewall, and additional features.
- Provides comprehensive protection for all endpoints.
- Includes threat detection, response, and management.
Performance Impact
Antivirus software can impact system performance. It continuously scans files and applications.
- May slow down the device during scans.
- Requires regular updates for optimal performance.
Firewalls usually have minimal impact on performance. They filter traffic without significant system resource usage.
- Operate at the network level.
- Do not slow down individual devices.
Endpoint Security solutions can vary in performance impact. They integrate multiple security features.
- Performance depends on the complexity of the solution.
- May require more resources than standalone antivirus or firewall.
Comparison Table
| Feature | Antivirus | Firewall | Endpoint Security |
|---|---|---|---|
| Scope | Individual Device | Network Level | Comprehensive |
| Performance Impact | Moderate | Low | Varies |
| Protection | Malware | Unauthorized Access | Multiple Threats |
Use Cases For Each Security Solution
Understanding when to use Endpoint Security, Antivirus, and Firewall is crucial. Each solution serves distinct purposes, enhancing your overall security strategy. Let’s explore the specific use cases for each security solution.
When To Use Endpoint Security
Endpoint Security is ideal for businesses with multiple devices. It protects against threats across all endpoints like laptops, smartphones, and tablets.
- Organizations with remote workers
- Companies handling sensitive data
- Businesses requiring centralized management
Endpoint Security also offers advanced features like data loss prevention and device control.
When To Use Antivirus
Antivirus software is essential for basic protection. It scans and removes malware from individual devices.
- Home users
- Small businesses
- Devices with internet access
Antivirus software is straightforward and easy to use. It is perfect for those needing simple yet effective protection.
When To Use Firewall
Firewall solutions are critical for controlling network traffic. They filter incoming and outgoing data to block unauthorized access.
- Network security for businesses
- Protecting internal networks
- Preventing unauthorized access
Firewalls are essential for safeguarding network perimeters. They are particularly useful in environments with multiple connected devices.
| Security Solution | Ideal For | Main Features |
|---|---|---|
| Endpoint Security | Businesses with multiple devices | Data loss prevention, device control |
| Antivirus | Home users, small businesses | Malware scanning, removal |
| Firewall | Network security, internal networks | Traffic filtering, unauthorized access prevention |
Integrated Security Approach
In today’s digital world, having a robust security system is essential. Many businesses rely on an Integrated Security Approach to protect their data. This approach combines various security solutions to build a strong defense. Let’s explore how combining endpoint security, antivirus, and firewalls can enhance your protection.
Combining Solutions
An integrated security approach blends multiple tools into one system. This ensures that each layer complements the other. Endpoint security protects devices like laptops and phones. Antivirus software detects and removes malware. Firewalls block unauthorized access to networks.
Combining these solutions creates a more comprehensive defense. It covers different aspects of your security needs. Each tool has its own strengths and weaknesses. By integrating them, you get a balanced protection system.
Benefits Of A Multi-layered Defense
A multi-layered defense system offers several benefits. First, it reduces the risk of cyber threats. With multiple layers, threats have a harder time penetrating your defenses.
Second, it ensures that if one layer fails, others can still protect you. For instance, if an antivirus misses a threat, the firewall can block it. This redundancy makes your security system more reliable.
Third, integrated security systems are easier to manage. You can monitor and control all layers from one dashboard. This saves time and reduces complexity.
| Solution | Main Function |
|---|---|
| Endpoint Security | Protects devices like laptops and phones |
| Antivirus | Detects and removes malware |
| Firewall | Blocks unauthorized access to networks |
In conclusion, an Integrated Security Approach is the best way to protect your data. It combines the strengths of endpoint security, antivirus, and firewalls. This creates a robust and reliable security system.
Choosing The Right Solution
Choosing the right security solution can be challenging. Each option—endpoint security, antivirus, and firewall—offers unique benefits. Understanding these solutions helps to make the best choice for your needs.
Factors To Consider
Several factors influence your decision. Consider these key points:
- Type of Threats: Identify the threats you face.
- System Complexity: Evaluate your system’s complexity.
- Budget: Determine your budget for security solutions.
- Ease of Use: Ensure the solution is user-friendly.
- Scalability: Check if the solution can grow with your needs.
Recommendations
Based on the factors above, here are some recommendations:
- For Basic Protection: Use an antivirus program. It detects and removes malware.
- For Network Security: Deploy a firewall. It monitors and controls incoming and outgoing network traffic.
- For Comprehensive Security: Implement endpoint security. It offers a broad range of protections, including antivirus and firewall features.
Here’s a quick comparison table:
| Solution | Best For | Main Features |
|---|---|---|
| Antivirus | Basic malware protection | Virus detection, removal |
| Firewall | Network security | Traffic monitoring, control |
| Endpoint Security | Comprehensive protection | Antivirus, firewall, more |

Credit: www.blumira.com
Future Trends In Digital Security
The digital landscape is evolving rapidly. Future trends in digital security are crucial for businesses. Understanding these trends can protect sensitive data and systems.
Emerging Threats
New types of cyber-attacks are emerging daily. These threats are getting more sophisticated. Hackers use ransomware to lock files and demand payment. Phishing attacks trick users into giving personal information. Malware can harm devices and steal data.
- Ransomware
- Phishing
- Malware
Cybercriminals are using AI to create smarter attacks. They can bypass traditional defenses. Businesses must stay alert to these new threats. Investing in advanced security measures is essential.
Technological Advancements
Technology is also advancing to counter these threats. Endpoint security solutions are becoming smarter. They use machine learning to detect unusual activities. This helps in identifying potential threats early.
Firewalls are getting more advanced too. Modern firewalls can filter traffic based on behavior. They can block suspicious activities before they reach the network. Antivirus software is evolving as well. It now includes real-time scanning and automatic updates.
| Technology | Advancement |
|---|---|
| Endpoint Security | Machine Learning |
| Firewalls | Behavior-Based Filtering |
| Antivirus | Real-Time Scanning |
Businesses should adopt these new technologies. This can help in safeguarding their data and systems. Staying updated with the latest security trends is key.
Frequently Asked Questions
What Is The Difference Between Firewall And Endpoint Security?
A firewall controls network traffic, blocking unauthorized access. Endpoint security protects individual devices from threats like malware and viruses. Both are essential for comprehensive cybersecurity.
What Is The Difference Between Endpoint Security And Antivirus?
Endpoint security protects all devices on a network, including laptops, phones, and tablets. Antivirus focuses on detecting and removing malware from individual devices. Endpoint security offers broader protection, including firewalls and intrusion detection.
Do I Need Antivirus If I Have Endpoint Security?
Yes, you still need antivirus. Endpoint security offers broader protection, but antivirus specifically targets and removes malware. Combining both enhances your security.
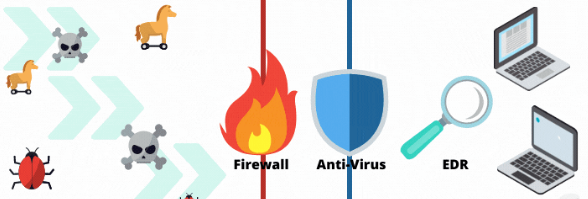
What Are The Three Main Types Of Endpoint Security?
The three main types of endpoint security are antivirus software, endpoint detection and response (EDR), and data loss prevention (DLP). These tools protect devices from malware, detect and respond to threats, and prevent data breaches.
Conclusion
Choosing between endpoint security, antivirus, and firewall depends on your specific needs. Each offers unique protection levels. Endpoint security provides comprehensive coverage, antivirus focuses on malware, and firewalls block unauthorized access. Combining all three ensures robust defense for your system.
Prioritize your requirements and select accordingly for optimal security.