Proactive security tools help identify and mitigate threats before they cause harm. They enhance overall system security by preemptively addressing vulnerabilities.
Proactive security tools are essential in modern cybersecurity. These tools continuously monitor systems to detect potential threats. They prevent breaches by identifying vulnerabilities early. Businesses rely on them to maintain robust security postures. Proactive tools include firewalls, intrusion detection systems, and antivirus software.
They offer real-time alerts and automated responses. This ensures swift action against potential risks. Implementing proactive security measures is crucial for safeguarding sensitive data. It also helps in maintaining regulatory compliance. Investing in these tools can save businesses from costly breaches and data loss. Their role is vital in today’s digital landscape.
Importance Of Proactive Security
Proactive security tools are essential in today’s digital world. They help prevent cyber threats before they cause harm. Reacting to threats after they occur is not enough. Being proactive means staying one step ahead of hackers.
Changing Threat Landscape
The digital world is always changing. New threats appear every day. Cybercriminals use advanced techniques. They look for vulnerabilities in systems. Traditional security methods can’t keep up. Proactive tools adapt to new threats quickly.
| Threat Type | Description |
|---|---|
| Malware | Malicious software that harms devices. |
| Phishing | Tricking users to steal information. |
| Ransomware | Encrypts files and demands payment. |
Risks Of Reactive Measures
Reacting to threats after they occur is risky. Damage is already done. Data can be lost or stolen. Businesses can lose money and reputation. Proactive security tools prevent these issues.
- Identify threats early.
- Prevent attacks before they happen.
- Reduce damage and recovery costs.
Using proactive tools is smart. It keeps systems safe and secure. Reacting to threats is not enough. Proactive security is the best approach.
Credit: expel.com
Types Of Proactive Security Tools
In the modern digital landscape, staying ahead of cyber threats is crucial. Proactive security tools help in identifying and mitigating threats before they cause damage. This section explores different types of proactive security tools, focusing on Intrusion Detection Systems and Security Information and Event Management.
Intrusion Detection Systems
Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity. They alert administrators to potential threats. IDS can be classified into two main types:
- Network-based IDS (NIDS): Monitors network traffic and analyzes it for suspicious activity.
- Host-based IDS (HIDS): Monitors a single host for suspicious activity.
IDS use signature-based detection or anomaly-based detection. Signature-based detection matches patterns in the network traffic. Anomaly-based detection identifies deviations from the normal behavior.
Security Information And Event Management
Security Information and Event Management (SIEM) tools collect and analyze log data. They provide real-time analysis of security alerts. SIEM tools offer the following features:
- Data aggregation from multiple sources
- Real-time monitoring and alerting
- Advanced analytics and reporting
SIEM helps in identifying and responding to threats quickly. By correlating events from various sources, it provides a comprehensive view of the security landscape.
Both IDS and SIEM are essential for a robust security strategy. They work together to identify and mitigate threats proactively.
Key Features To Look For
Proactive security tools are vital in today’s digital age. They help protect systems and data from potential threats. Understanding the key features of these tools ensures you choose the best one for your needs.
Real-time Monitoring
Real-time monitoring is a crucial feature in proactive security tools. It allows for the constant surveillance of your system. This feature helps in detecting and responding to threats immediately.
With real-time monitoring, you can:
- Identify threats as they occur.
- Receive instant alerts on suspicious activities.
- Analyze data continuously for anomalies.
This feature ensures that any potential issues are addressed swiftly. It minimizes damage and maintains system integrity.
Automated Response
Automated response is another essential feature. This allows the system to take immediate action when a threat is detected. It reduces the need for manual intervention.
Key benefits of automated response include:
- Quick isolation of affected areas.
- Automatic blocking of malicious IP addresses.
- Immediate execution of predefined security protocols.
Automated response ensures a swift reaction to threats. It helps in maintaining the security of your system with minimal delay.
Incorporating these features in your security tools can significantly enhance your protection mechanisms. Choose tools that offer real-time monitoring and automated response for optimal security.

Credit: www.bankinfosecurity.com
Implementing Proactive Security
Implementing proactive security is crucial for any business. It involves using advanced tools and techniques to prevent threats. This approach helps in identifying vulnerabilities before they are exploited. By being proactive, companies can secure their data, systems, and networks effectively.
Integration With Existing Systems
Integrating proactive security tools with existing systems is essential. This ensures smooth operation without disrupting current workflows. Companies can use APIs and plugins for seamless integration. This makes the implementation process easier and more efficient.
Here are some key benefits of integration:
- Improved Efficiency: Less manual intervention is needed.
- Enhanced Monitoring: Real-time alerts and automated responses.
- Cost-Effective: Reduces the need for multiple security tools.
Employee Training
Employee training is a vital part of proactive security. Well-trained staff can identify and prevent security threats. This reduces the risk of human error and enhances overall security.
Effective training programs should include:
- Regular Workshops: Keep employees updated on the latest threats.
- Hands-On Training: Practical exercises to reinforce learning.
- Assessment Tests: Evaluate the effectiveness of the training.
Investing in employee training is crucial for maintaining a secure environment. It empowers employees to be the first line of defense against security breaches.
Case Studies Of Success
Proactive security tools have transformed businesses worldwide. They prevent threats before they cause harm. Let’s explore some real-world success stories.
Small Business Examples
Small businesses often face unique security challenges. Here are two examples of small businesses that benefited from proactive security tools:
| Business | Challenge | Solution | Outcome |
|---|---|---|---|
| Local Bakery | Frequent phishing attacks | Implemented anti-phishing software | Reduced phishing incidents by 90% |
| Tech Startup | Data breaches | Deployed endpoint protection | Zero breaches in 12 months |
Enterprise Solutions
Large enterprises need robust security measures. Here are two successful implementations:
- Global Bank: Faced with sophisticated cyber threats, they used advanced threat detection tools. The result was a 50% reduction in security incidents.
- Retail Giant: Struggling with data theft, they employed a comprehensive security suite. This led to a 75% drop in data loss.
These case studies showcase how proactive security tools can safeguard businesses of any size. Implementing these tools can lead to significant improvements in security and peace of mind.
Challenges And Solutions
Proactive security tools are essential for safeguarding digital assets. However, they come with their own set of challenges. In this section, we will explore these challenges and their solutions.
Cost And Budgeting
One of the biggest challenges is the cost of these tools. Many organizations find it difficult to allocate sufficient budget for advanced security measures. Here are some tips to manage costs:
- Prioritize needs: Identify the most critical assets and focus on protecting them first.
- Leverage open-source tools: Many effective security tools are available for free.
- Opt for scalable solutions: Choose tools that can grow with your organization.
By following these strategies, you can manage costs without compromising on security.
Technical Complexity
Another challenge is the technical complexity of implementing these tools. Many of them require specialized knowledge and skills. Here are some ways to tackle this:
- Training: Invest in training for your IT staff to understand these tools.
- Consult experts: Hire consultants to help with the initial setup.
- Use user-friendly tools: Opt for solutions that offer intuitive interfaces.
These steps can help in overcoming technical hurdles and ensuring effective implementation.
Future Trends In Security
As technology continues to evolve, so does the landscape of cybersecurity. Proactive security tools are becoming essential in safeguarding against emerging threats. Let’s explore some of the future trends in security.
Ai And Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing cybersecurity. These technologies help in identifying patterns and predicting future threats.
- AI can analyze vast amounts of data quickly.
- ML improves the accuracy of threat detection.
- These tools can adapt to new threats in real-time.
With AI and ML, security systems can become more intelligent and adaptive. They can learn from past incidents and prevent similar threats in the future.
Advanced Threat Detection
Advanced Threat Detection is crucial for modern cybersecurity. This involves using sophisticated tools to identify complex threats.
| Tool | Function |
|---|---|
| Intrusion Detection Systems (IDS) | Detects unauthorized access |
| Endpoint Detection and Response (EDR) | Monitors end-user devices |
These tools help in identifying anomalies and potential attacks. They provide real-time alerts and detailed reports, making it easier to respond quickly.
Using advanced threat detection tools ensures that organizations stay one step ahead of cybercriminals.
Choosing The Right Tools
Choosing the right proactive security tools is crucial for safeguarding your digital assets. With many options available, it’s essential to make an informed decision. This section will guide you through key considerations for selecting the best tools.
Vendor Comparisons
Comparing vendors can be overwhelming. To simplify, focus on these aspects:
- Reputation: Choose vendors with a strong track record.
- Support: Ensure they offer 24/7 customer support.
- Features: List essential features your business needs.
- Cost: Compare pricing plans and hidden fees.
| Vendor | Reputation | Support | Features | Cost |
|---|---|---|---|---|
| Vendor A | High | 24/7 | Advanced | $$$ |
| Vendor B | Medium | Business Hours | Basic | $$ |
| Vendor C | High | 24/7 | Comprehensive | $$$$ |
Custom Vs. Off-the-shelf
Deciding between custom and off-the-shelf solutions depends on your needs:
- Custom Solutions:
- Tailored to your specific requirements
- Higher initial costs but flexible
- Longer development time
- Off-the-Shelf Solutions:
- Ready to use immediately
- Lower upfront costs
- May not meet all your needs
Weigh the benefits and drawbacks of each option. Choose what best fits your business model and budget. Custom solutions offer flexibility but come at a cost. Off-the-shelf options are quick and budget-friendly but less tailored.

Credit: www.opsmx.com
Frequently Asked Questions
What Is The Proactive Security Model?
A proactive security model identifies and mitigates potential threats before they cause harm. It emphasizes prevention, continuous monitoring, and quick response. This approach reduces vulnerabilities and enhances overall security.
What Is A Proactive Approach To Security?
A proactive approach to security involves anticipating threats and taking preventive measures. It includes regular updates, monitoring, and employee training. This method reduces risks and enhances overall protection.
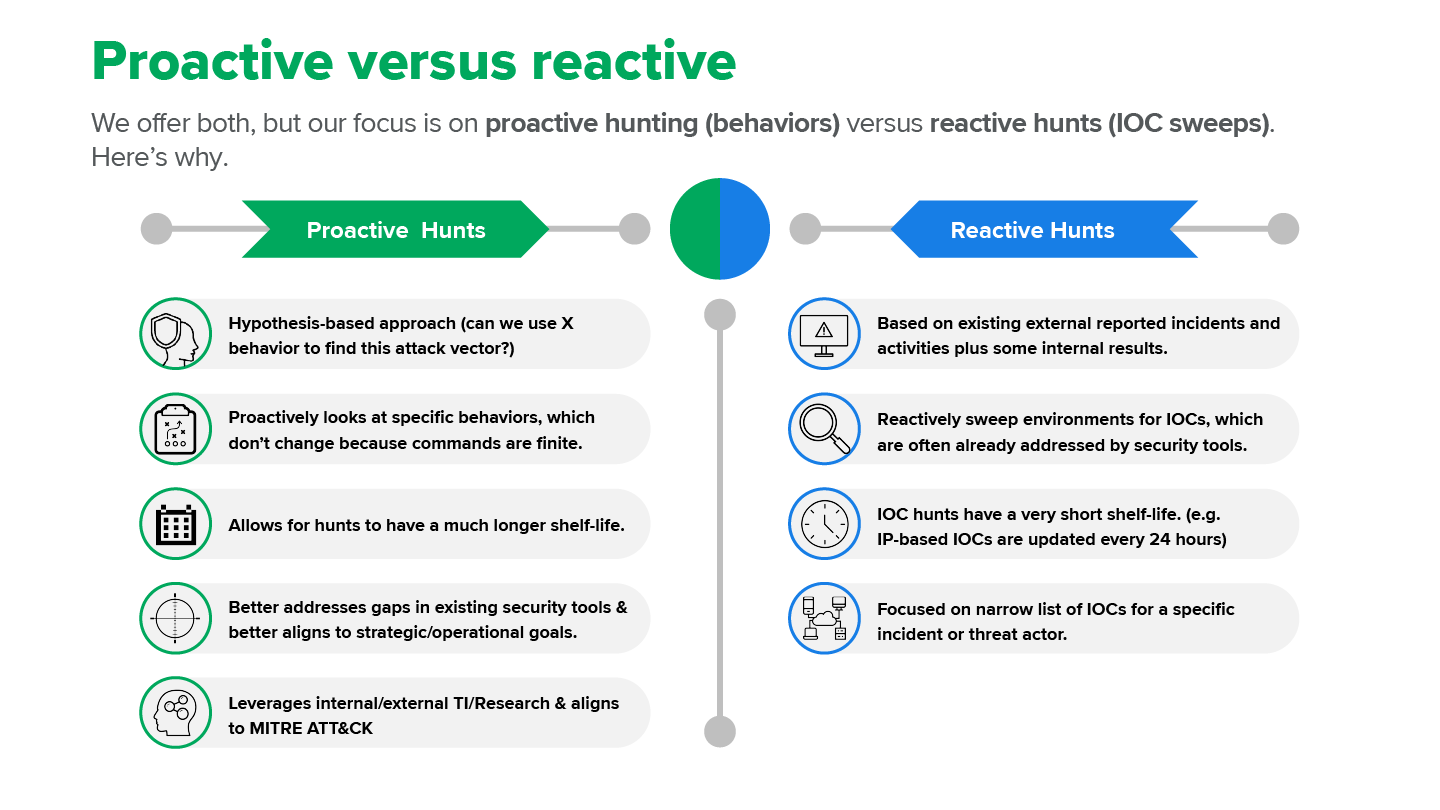
What Is The Difference Between Proactive And Reactive Security?
Proactive security involves preventing threats before they occur. Reactive security responds to incidents after they happen. Proactive measures include regular updates and monitoring. Reactive measures include incident response and recovery. Both are essential for comprehensive protection.
What Are The Three Security Tools?
Three essential security tools are antivirus software, firewalls, and encryption tools. These protect against malware, unauthorized access, and data breaches.
Conclusion
Proactive security tools are essential for safeguarding your digital assets. They provide early threat detection and robust protection. Implementing these tools ensures a more secure environment. Invest in proactive security to stay ahead of potential risks. Enhance your cybersecurity strategy today to maintain peace of mind.

